
Photo by Martha Dominguez de Gouveia on Unsplash
Digital Signatures - a Starter for Ten
A very basic intro for complete beginners. Part of the Starter for Ten series.
What is a digital signature?
When something (for example a file, some text, a video, a message) is sent electronically, a digital signature is used to check that the thing hasn't been tampered with.
Before we get on to signatures, we need to talk about 'message digest'….
Using some clever technology, you can generate a unique bunch of numbers and letters that represent the something that is being sent.
Say the text that is being sent is 'My name is Jen'. Using an online generator, I can get a unique string of numbers and letters that represent that text:
057fed8fa07d5e6954acba27a426d922
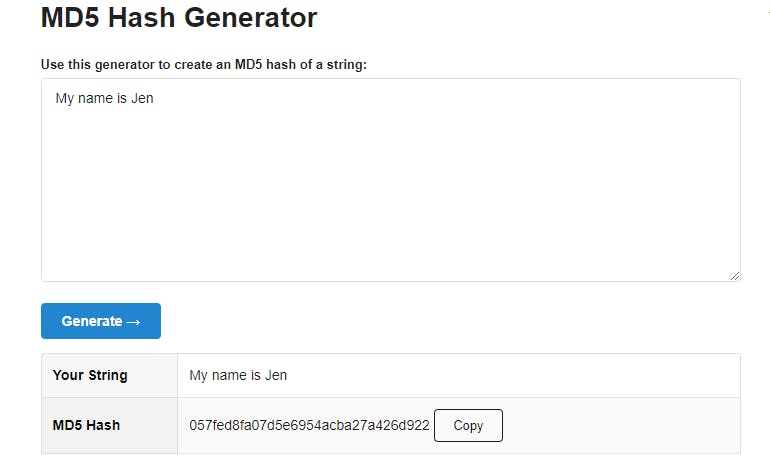
If I were to generate the string again, using the exact same text, I would get the exact same string.
Think of it as a fingerprint for that text. As long as the text doesn't change, the string won't change.
However, if I changed the text, even by one letter, and generated the string again, it would be different:
715777f327b876b1092486d415380700
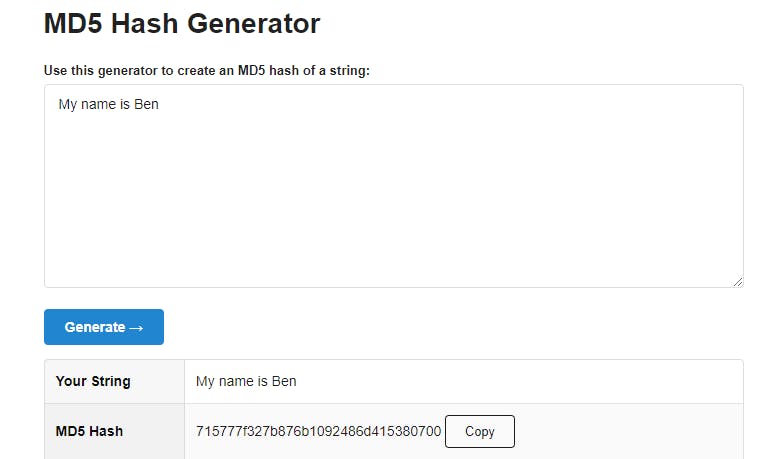
This string of numbers and letters is known as the message digest. It is also sometimes also called hash value, digest, or simply hash. It is also known as a checksum when it is used for checking whether a file/text/message has been tampered with.
There are many different 'flavours' of message digest. MD5 is one of the most common and the message digest is often referred to as the 'MD5 hash', as in the images above. SHA-1, SHA-256 and SHA-512 are other examples.
Try generating message digests for your own text using the following website: https://www.md5hashgenerator.com/
To generate a message digest for a file, rather than text, you can use the md5sum tool (on Linux Ubuntu) by running the command md5sum {filename}:
// Create a new file
$ echo 'Hello World' > myfile.text
// Generate a message digest for the file
$ md5sum myfile.txt
// The message digest is printed to the screen
2140073af936af8bda960868a161385e myfile.txt
So what is a digital signature?
Now that we understand what a message digest is and how it is created we can move on to digital signatures.
So we have the thing that we want to send electronically - let's say it is a file. We have generated a message digest for that file and let's say it looks like this:
4ef1309532bb95b92f665ded2f78902a
Now, to make things even more secure, so we can be extra sure nobody has tampered with our file while it was being sent, we can encrypt the message digest itself. The encrypted message digest is then known as a digital signature.
So then what?
Here's an example of how this might work in real life:
Let's say I want to send a file to Joe. When Joe receives the file, he wants to know that it hasn't been tampered with.
Before sending it, I generate a message digest (aka hash or checksum) for the file. I then encrypt the message digest using a private key. This message digest is now a digital signature.
I send Joe the original file, along with the digital signature and the public key that goes with the private key I used.
When he receives the file, signature and public key, Joe can decrypt the signature to get the message digest. He can then generate a new message digest for the file that has been received and check that it matches the original message digest/signature I sent and he decrypted. If those two match, we can be confident that the file hasn't been tampered with.
We're not quite done yet though; let's add another layer…..
Digital certificates and public key identity
How does Joe know that the public key he's received is legit and genuinely came from me? The answer is digital certificates. A digital certificate certifies that the public key is associated with a particular identity. In this case, mine.
For more information on digital certificates in particular, this is a useful article (see section 3): https://www.baeldung.com/java-digital-signature
Further reading:
